
We recently reported that Apple was working on a fix for a Safari bug that led to the leaking of users’ browsing history and Google ID. Luckily it seems that Apple was able to fix the bug with iOS 15.3 RC and macOS Monterey 12.2 RC, which were both released on Thursday to developers and beta users.
The bug was first discovered by FingerprintJS, which revealed that websites could use an exploit found in IndexedDB (a Javascript API used for storing data) to access URLs recently visited by a user and even obtain the user’s Google ID and related personal data.
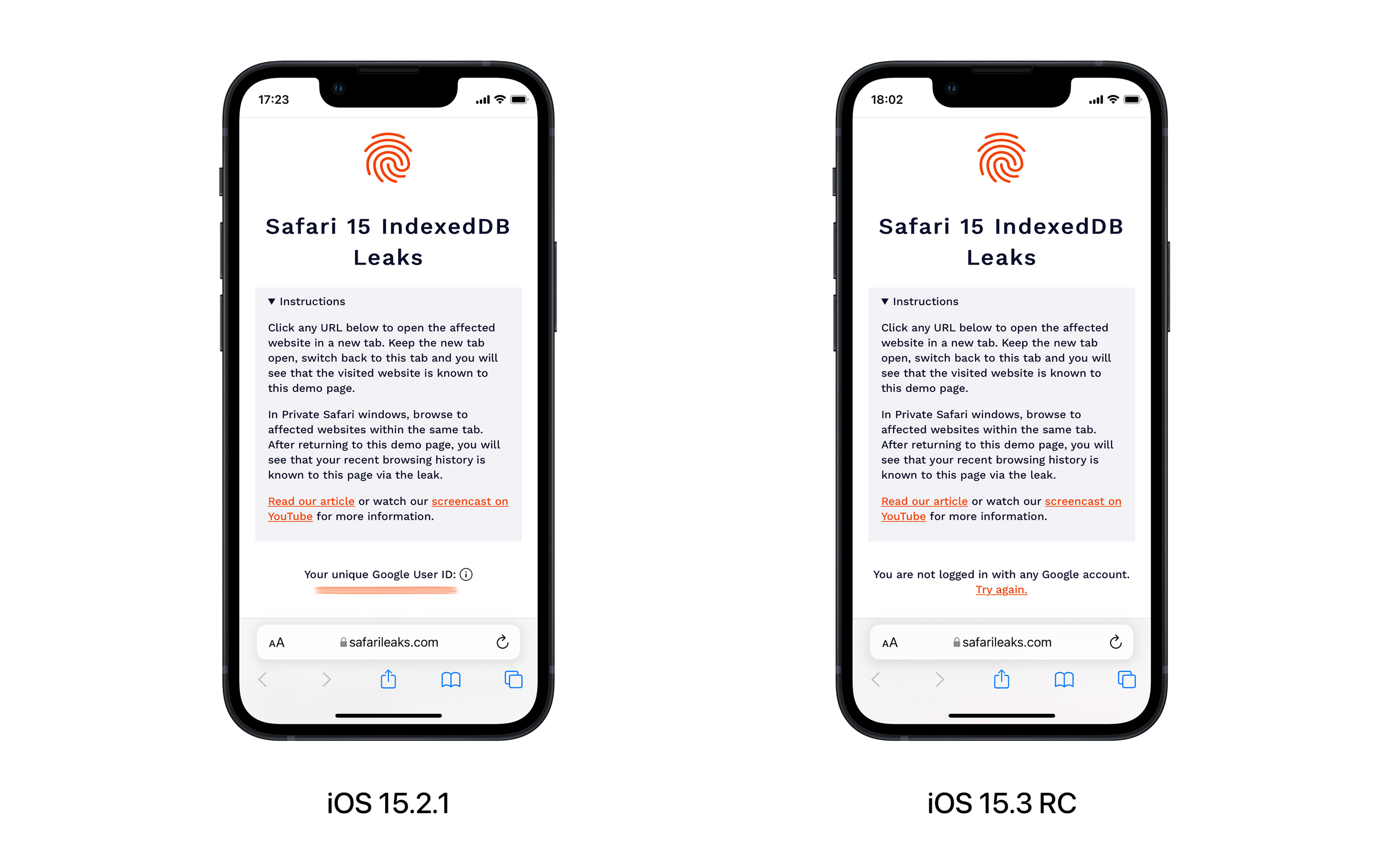
However, our tests suggest that the exploit has been fixed with iOS 15.3 and macOS Monterey 12.2. FingerprintJS has built a demo website to show how the bug works in action, and anyone can access the website to see how it knows some of the URLs you have recently visited and details about your Google Account.
When running the same tests on devices updated to iOS 15.3 RC and macOS 12.2 RC, the website shows no data and says that the user is not logged into a Google Account.
According to FingerprintJS, the exploit affected all the iOS 15 and macOS Monterey releases prior to today’s builds. iOS 14 was not affected by the bug, as well as users who still have Safari 14 on Macs running versions prior to macOS Monterey.
There’s no word from Apple on when iOS 15.3 and macOS Monterey 12.2 will be officially released to the public, but we expect that the updates will be made available to everyone in the next few days as the company has already rolled out Release Candidate (RC) builds for testing.
Author: Filipe Espósito
Source: 9TO5Google



